In the particular ever-evolving landscape society development, maintaining computer code integrity is essential to ensure the reliability, safety measures, and gratification of programs. Code integrity refers to the confidence that the computer code remains unaltered and functions as designed from development via deployment. Implementing best practices for preserving code integrity may help prevent bugs, vulnerabilities, and other issues that can come up during the software lifecycle. This informative article explores important strategies to uphold signal integrity during development and deployment.
1. Version Control Systems (VCS)
Using Version Handle
A Variation Control System (VCS) like Git is indispensable for checking changes, collaborating together with team members, in addition to managing different variations of code. VCS allows developers to be able to revert to previous states, compare adjustments, and merge up-dates efficiently.
Branching plus Merging Strategies
Function Branching: Create independent branches for each feature, bug fix, or task. This particular isolates changes till these are ready to be integrated.
Mainline Development: Maintain the stable main part (often called main or master) in addition to merge changes just after thorough screening.
Pull Requests (PRs): Use PRs intended for code reviews and even discussions before joining changes. This assures multiple eyes around the code and helps catch potential problems early.
2. Computer code Evaluations
Peer Reviews
Code reviews are essential for maintaining code quality. They enable knowledge discussing, identify potential problems, and ensure faithfulness to coding specifications.
Automated Reviews
Combine automated code evaluation tools (e. gary the gadget guy., SonarQube, CodeClimate) to enforce coding specifications, detect security weaknesses, and identify program code smells. Automated evaluations complement peer testimonials by catching issues that might be unnoticed by humans.
three or more. Automated Testing
Device Screening
Write device tests to confirm individual pieces of the particular codebase. Unit tests aid ensure that every part functions effectively in isolation.
Incorporation Testing
Integration testing verify the relationships between different parts. They help determine issues that come up when individual pieces are combined.
End-to-End Tests
End-to-end tests simulate user cases to make certain the complete application works as anticipated. They are vital for catching issues that might not become apparent in device or integration testing.
Continuous Integration (CI)
Implement CI to run automated checks on every code change. CI tools (e. g., Jenkins, Travis CI, CircleCI) integrate with version control systems to automatically build and even test code, providing immediate feedback upon the impact regarding changes.
4. Static Code Research
Linting
Use linters in order to enforce coding specifications and catch syntax errors. Linters support maintain a steady code style and improve readability.
Stationary Analysis Tools
Use static analysis resources to detect prospective vulnerabilities, performance issues, and code quality problems. These resources analyze code with out executing it, offering insights into prospective issues early throughout the development method.
5. Secure Code Practices
Input Affirmation
Validate all input to prevent shot attacks (e. gary the gadget guy., SQL injection, cross-site scripting). Input acceptance ensures that only predicted data is refined by the application.
Authentication and Authorization
Carry out robust authentication plus authorization mechanisms to control use of hypersensitive parts of the application. Use industry-standard methods and libraries to take care of user authentication safely.
Data Encryption
Encrypt sensitive data in transit and with rest. Encryption safeguards data from unauthorized access and guarantees its integrity.
6th. Paperwork
Code Responses
Write clear and concise comments to explain the purpose in addition to functionality of computer code. Comments help various other developers understand the signal and its framework.
Documentation Tools
Work with tools like JSDoc, Sphinx, or Strut to generate thorough documentation for APIs and codebases. Good documentation ensures that developers can easily realize and utilize signal.
7. Environment Persistence
Configuration Administration
Work with configuration management tools (e. g., Ansible, Chef, Puppet) in order to ensure that almost all environments (development, screening, production) are steady. This minimizes environment-specific issues and guarantees that code acts the same way across different stages.
Containerization
Adopt containerization technologies like Docker to create consistent and even reproducible environments. Storage units encapsulate all dependencies, making it easier to set up and scale apps.
8. Continuous Deployment (CD)
Automated Application Pipelines
Implement DISC pipelines to systemize the deployment method. CD tools (e. g., Jenkins, GitLab CI/CD, Bamboo) help ensure that code is usually deployed reliably in addition to consistently.
Blue-Green Deployments
Use blue-green deployments to minimize downtime and even reduce risk throughout updates. This plan requires running two the same environments (blue and green) and switching traffic together throughout deployments.
Canary Produces
Perform canary emits by deploying fresh features to some sort of small subset involving users before some sort of full rollout. This specific allows monitoring for just about any issues before wider deployment.
9. Overseeing and Logging
Software Monitoring
Use overseeing tools (e. g., Prometheus, New Relic, Datadog) to monitor the performance and health of apps in real-time. Supervising helps detect and resolve issues rapidly.
Log Management
Implement centralized logging to be able to aggregate and analyze logs from distinct parts of the applying. Tools like ANTELOPE Stack (Elasticsearch, Logstash, Kibana) or Splunk help in determining trends and the diagnosis of issues.
10. read this Managing Programs
Develop incident management plans to handle unexpected concerns. Plans should outline steps for figuring out, diagnosing, and managing incidents.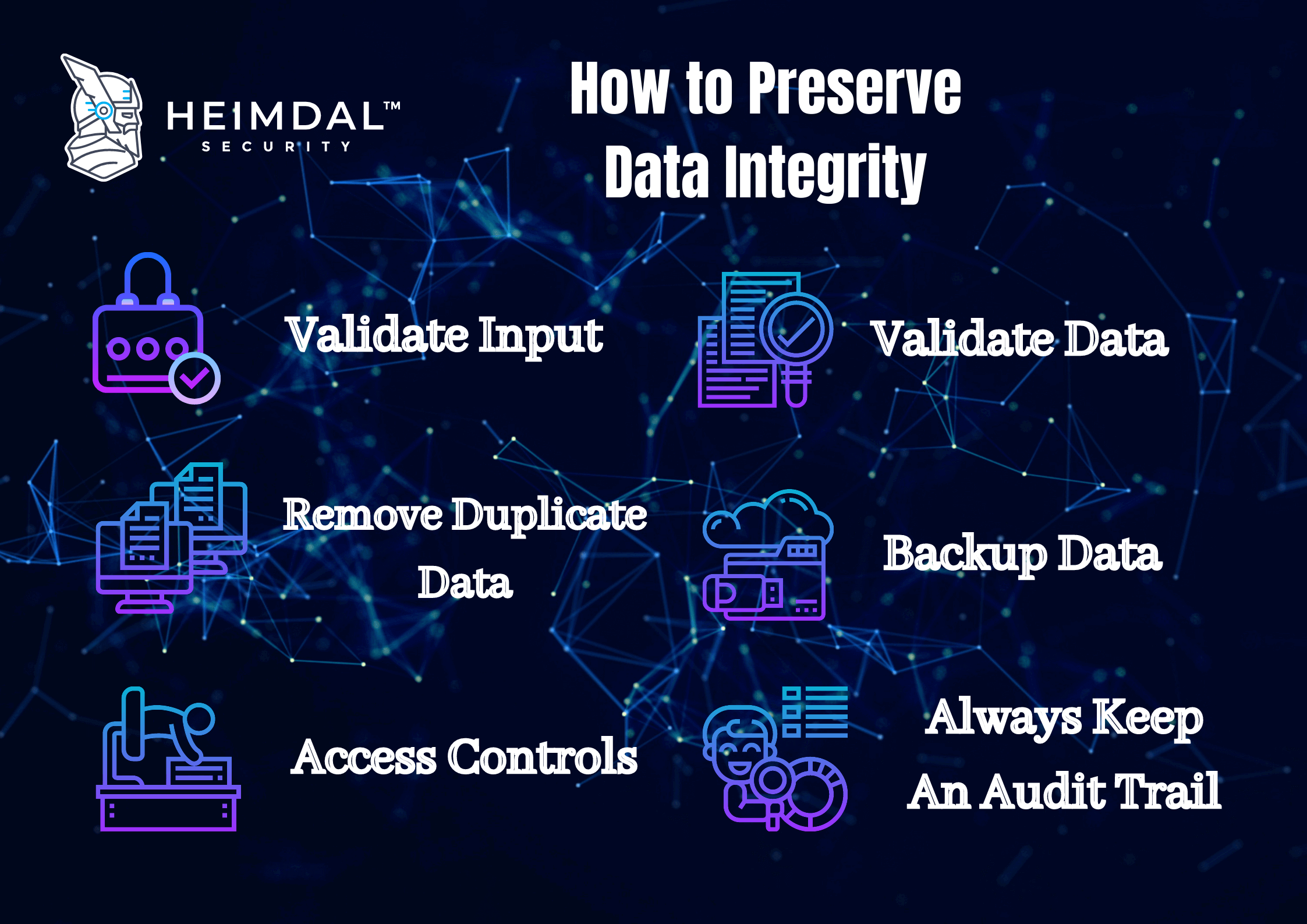
Post-Incident Opinions
Conduct post-incident testimonials to analyze the root cause of incidents preventing recurrence. Doc lessons learned in addition to update processes consequently.
Conclusion
Maintaining program code integrity in growth and deployment will be a multifaceted obstacle that requires a combination of best practices, tools, and a proactive mindset. Simply by leveraging version manage, code reviews, computerized testing, static evaluation, secure coding procedures, documentation, environment uniformity, continuous deployment, overseeing, and incident reaction, development teams can ensure that their own code remains trusted, secure, and leistungsfähig throughout its lifecycle. Adopting these finest practices not just enhances code honesty and also contributes to be able to the overall accomplishment and sustainability of software projects.
